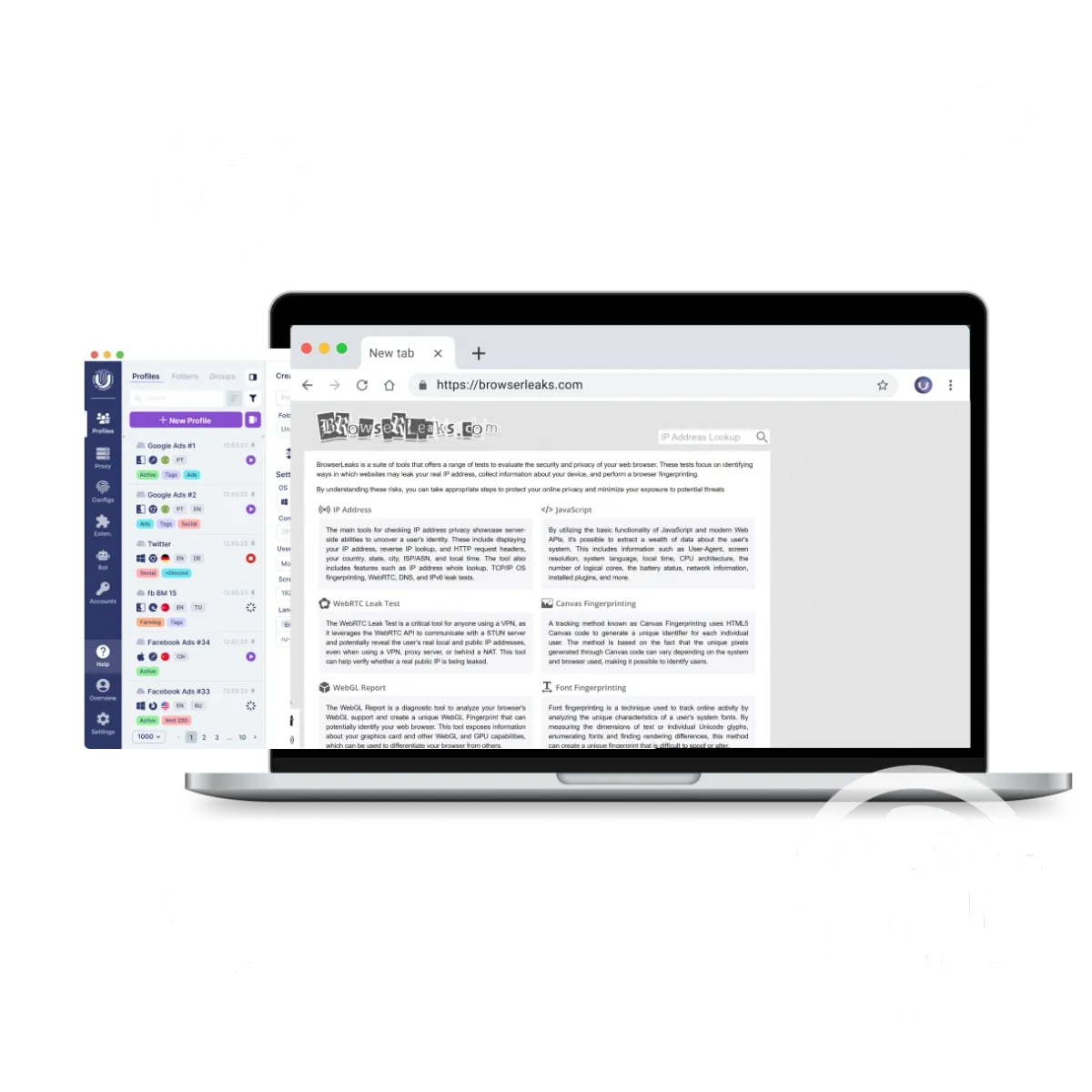
Use the secure anti-detect browser Undetectable to create unique profiles for each account: set different IP addresses, languages and time zones, and simulate different devices (smartphones, PCs). This helps websites treat each profile as a separate user. For example, when managing multiple social accounts you can create profiles with IPs from different countries to avoid suspicion of multi-accounting.
After configuring, test the profiles with the BrowserLeaks.com anonymity testing service. It will show whether you accidentally reveal your real location or other data. If leaks are found (for example, an IP “shows up” via DNS), adjust settings in Undetectable.io: change the proxy (consider using residential proxies) or add randomized browser parameters. Think of this as regular maintenance for your digital privacy.
Tracking technologies change, so check your profiles via BrowserLeaks regularly. Update the anti-detect browser settings in Undetectable if sites begin blocking accounts, and disable unnecessary features. This way you keep control of your digital security even as detection algorithms get smarter.