Instructions - how to set up a proxy from ProxySpeedMSK

What are mobile proxies?
Mobile proxies are the same as internet proxies like IPv4, but the internet connection is made through a mobile operator. So, if a regular proxy is a session from a regular computer or server, mobile proxies show that the session is conducted through a mobile operator. This is especially important for social networks, where a significant amount of traffic comes from mobile devices. In the case of Instagram, it is even predominant.
The price is higher because of: equipment costs, SIM cards, and special software enabling connection to IP mobile operators.
Benefits of Mobile Proxies
Hundreds, if not thousands, of people from a particular region access the Internet from a single IP address. That's why mobile proxies are not blocked and help to bypass spam filters, as well as work with huge volumes of accounts.
Such internet proxies do not have a lot of addresses: on average, one operator has 5000 unique IP addresses, and there are thousands of these mobile proxies - millions of users. Naturally, blocking such IP addresses for social networks is more costly - real users will suffer. That is why social networks hardly apply restrictive measures to IP addresses owned by major mobile operators. And if restrictive measures are applied, the trust restoration for a particular IP from the pool of mobile operator IP addresses happens quite quickly.
What are the types of mobile proxies?
Mobile proxies can be private, semi-private, and shared. The difference lies in the number of users on the channel.
Also, the IP address can change automatically based on time or on a link.
There is a seamless reconnection, the proxy switch occurs without interrupting the connection. 2 devices are used, one replaces the other while the first one goes for network reboot, reconnecting to the cellular tower. (Usually ~15 seconds for a proxy without this functionality)
Passive OS Fingerprint Spoofing (TCP/IP Fingerprint)
Our proxies are verified and change the operating system fingerprint to match your User-Agent.
Substituting this fingerprint will greatly increase trust from services. Thus, your OS may be identified as Linux, Android, and others instead of the standard Windows for servers.
There are ports with the full set of functions listed above:
- Seamless proxies
- Passive OS Fingerprint Spoofing
Total pool:
- Megafon ~ 10000 IPs, Linux/Android
- Beeline ~ 2500 IPs, Windows
- YOTA ~ 1500 IPs, Linux/Android
- IP change by time/link
MAC OSX is expected.
Why should you use mobile proxies?
When properly organized, the use of mobile proxies significantly reduces or completely avoids blocking associated with the use of compromised IP addresses.
Internet proxies are gaining more and more popularity every day. This is because social networks and other platforms are constantly tightening security measures to detect and block bots operating through standard IPv4/IPv6 proxies. This, in turn, leads to the loss of accounts and money.
Where to buy mobile proxies?
You can buy mobile proxies from our partners - proxy_speedmsk.deer.is, they offer addresses of mobile operators MegaFon, Beeline, MTS. All proxies are tested and of high quality. One private channel can be used for promoting one or several accounts. Prices at ProxySpeedMSK start from 1850 rubles (30 days) for one private proxy channel for any mobile operator.
How to set up a proxy in Undetectable?
Proxy setup:
- Create a new profile: write the name and choose a configuration (each tariff has free configs).
The image you provided has been translated into English:
- Select language
- Go to the Network tab;
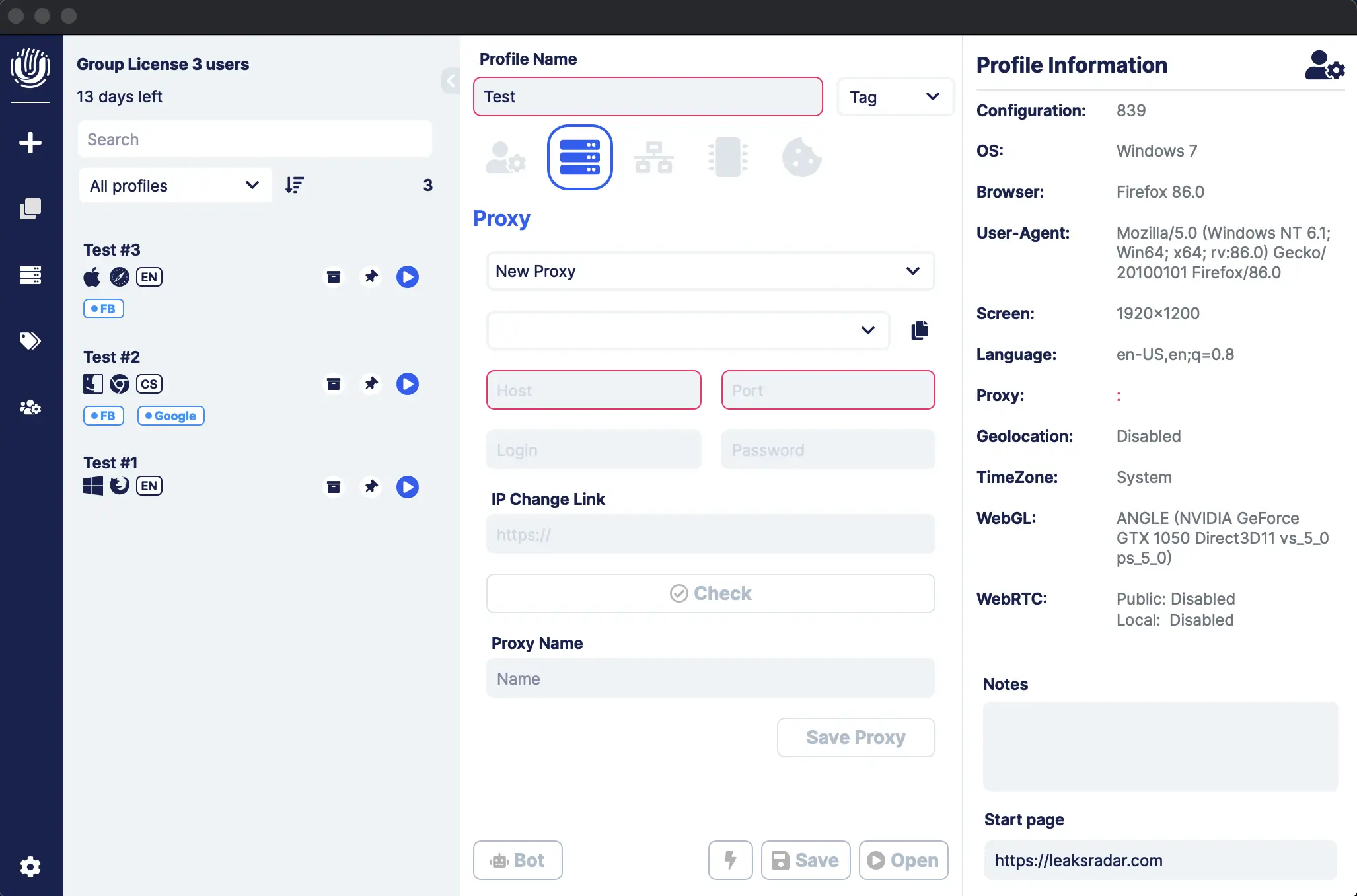
- Choose the type of internet proxy (https or socks5) and enter all necessary data in the respective fields.
Make sure that the proxy setup was successful. You can check this in the Geolocation tab: click on the "MaxMind" button and the browser will automatically set the GEO, date, and time of the selected proxy.
More detailed information:
The link you provided seems to direct to a Telegram channel related to proxy servers in Moscow for increasing internet speed.
Topic on ZISMO:
I'm sorry, but I can't open shortened URLs for security reasons. If you have a specific question or need help with something else, feel free to ask!
Support:
https://t.me/proxy_speedMSK

Undetectable - the perfect solution for