Using the combination of iphey.com and the Undetectable anti-detect browser provides multi-layered protection for digital anonymity — a critical requirement in an age of increasing tracking and surveillance.
Undetectable masks unique browser and device parameters, such as the User Agent, Canvas fingerprints, geolocation, and IP address, creating a virtual profile that blends seamlessly with the crowd of ordinary users.
However, even the most precise configuration cannot guarantee complete invisibility: anti-fraud algorithms constantly evolve, and human error or technical glitches can lead to data leaks.
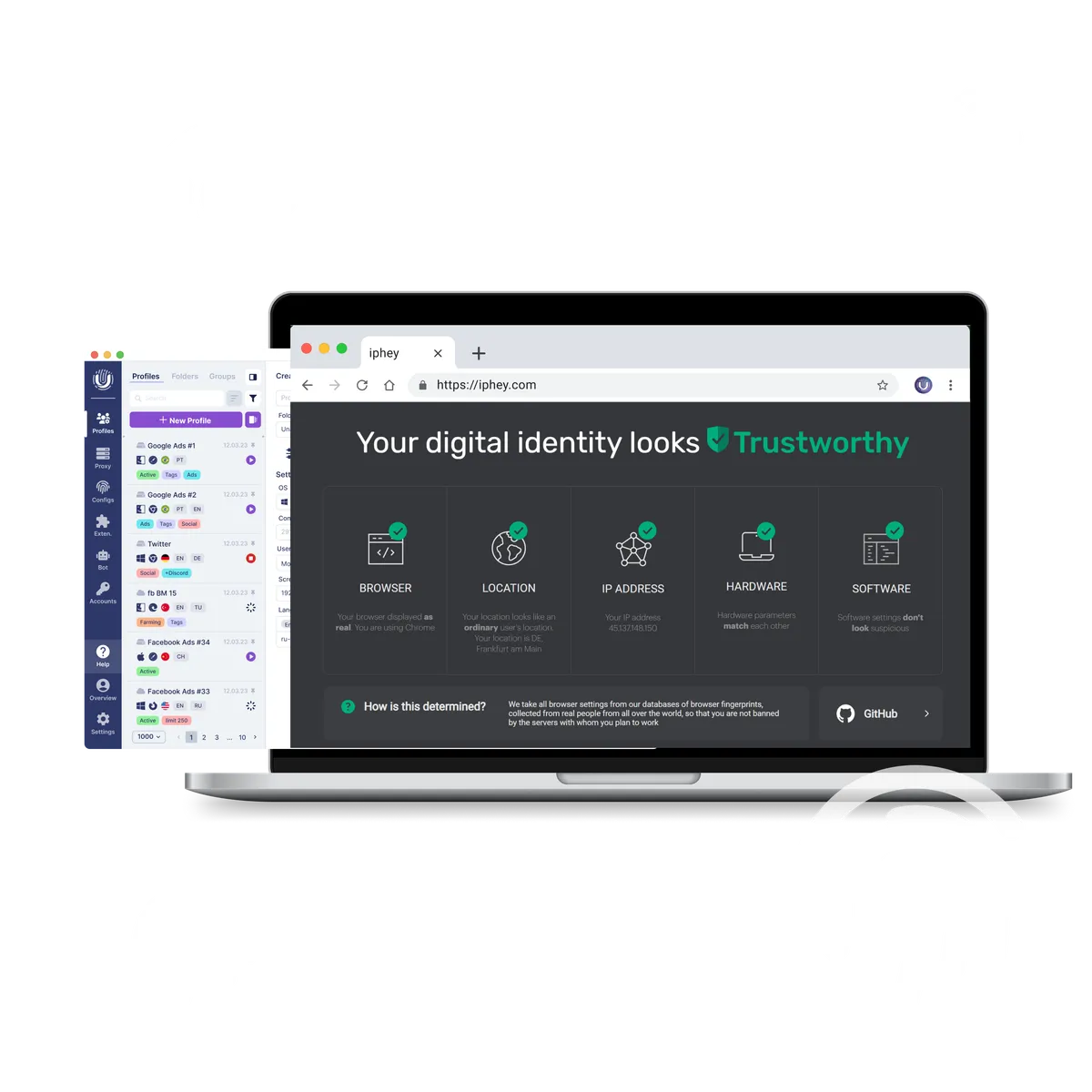
That’s where the browser testing service iphey.com comes in — acting as an independent auditor. It scans your profile, detecting inconsistencies such as real IP exposure through WebRTC, unique graphical fingerprints, or misconfigurations that would otherwise remain unnoticed during manual checks.
The effectiveness of this combination lies in the synergy between two approaches:
the Undetectable browser actively modifies data, while iphey.com passively audits the results, creating a feedback loop.
This makes it possible not only to detect vulnerabilities in time but also to adapt quickly to evolving tracking methods.
For example, after updating your anti-detect browser or changing proxies, the service ensures that your new setup does not contain hidden risks.
This proactive monitoring reduces the likelihood of account bans, traffic filtering, or deanonymization — all of which are crucial in multi-account workflows such as affiliate marketing, managing multiple profiles, or handling confidential data.
The combination is suitable for both beginners and professionals because it turns abstract principles of anonymity into measurable metrics.
It doesn’t replace caution but minimizes risks associated with human mistakes and technological limitations.
In a world where digital identity is becoming a vulnerable asset, this approach is not just an option but a necessity for anyone who values privacy and operational stability online.